HTTPS 服務的入口,在K8s環境中當然不可缺少入口與憑證兩大元素,關於"入口",可以在此篇文章中複習下~
在K8s環境中,印行憑證管理、或者透過申請,蠻好用的一個控制器就是 cert-manager
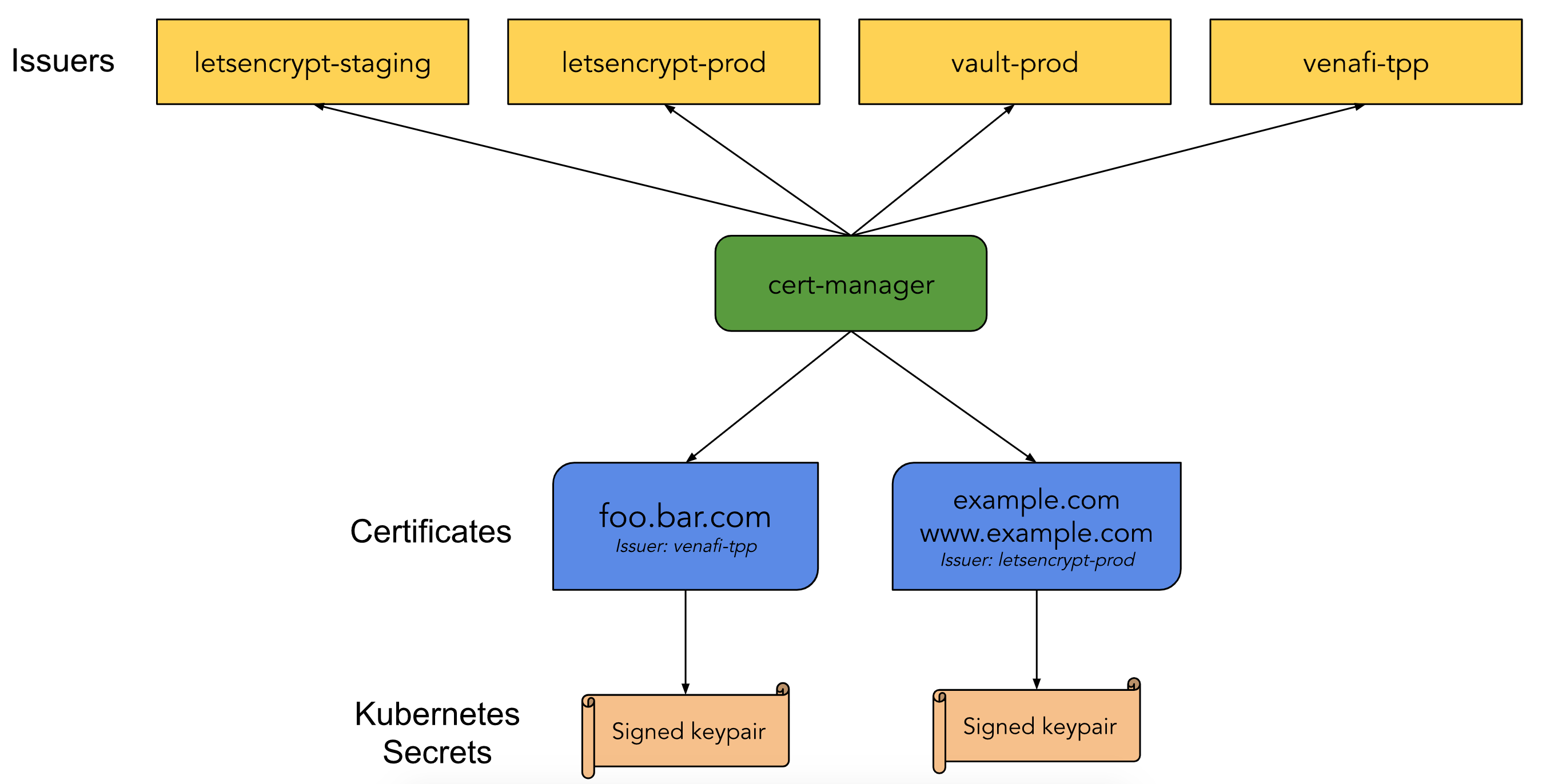
從上圖中,主要兩個新元素資源:Issuer、Certificates
其用途是 憑證(x509 certificates) 申請機構代表,例如 Let’s Encrypt
其中定義了機構的窗口(server)、申請者(email)、申請方式(HTTP01 or DNS01)等等,概念如下:
apiVersion: certmanager.k8s.io/v1alpha1
kind: Issuer
metadata:
name: letsencrypt-prod
namespace: edge-services
spec:
acme:
# The ACME server URL
server: https://acme-v02.api.letsencrypt.org/directory
# Email address used for ACME registration
email: user@example.com
# Name of a secret used to store the ACME account private key
privateKeySecretRef:
name: letsencrypt-prod
# Enable HTTP01 validations
http01: {}
此資源用途可以想像為憑證申請表的意思~
其內容定義:申請網域or網址(dnsNames、acme)、指定憑證發行機構(issuerRef),概念如下:
apiVersion: certmanager.k8s.io/v1alpha1
kind: Certificate
metadata:
name: acme-crt
spec:
secretName: acme-crt-secret
dnsNames:
- foo.example.com
- bar.example.com
acme:
config:
- http01:
ingressClass: nginx
domains:
- foo.example.com
- bar.example.com
issuerRef:
name: letsencrypt-prod
# We can reference ClusterIssuers by changing the kind here.
# The default value is Issuer (i.e. a locally namespaced Issuer)
kind: Issuer
以上,當您定義好兩項資源與套用後,即可向憑證商提出申請,如順利即可獲得您網站所需的 SSL 憑證。此憑證最終會存放於K8s Secret資源中。
